In a previous tutorial, I explained how to perform SQL injection attack using DVWA. Now in this tutorial, we will be going to see how CSRF work and how this could be exploited. In CSRF a user is forced to perform unwanted actions on the web application in which they are unauthenticated. You can trick the user with the help of social engineering attacks to perform these actions. In CSRF attack the state changing requests are targeted. There is no intention to theft the data. Now, most of the web applications like Joomla, Wordpress, Struts, Spring, and .NET have built-in CSRF supports. If no protection is used, the site will have no way to differentiate between the requests of the user or the attacker. Sometimes CSRF attacks are stored on the sites itself. This is called stored CSRF. This could be done by storing IMG or IFRAME tag in a field that accepts HTML. Many web application accepts POST requests only to prevent CSRF attacks, but there are many other ways to compromise this type of security. Now we will test CSRF attack on DVWA to see how it works.
Let’s Start,
First of all, you need to install DVWA on Kali machine if you don’t know how to install DVWA you can check that here.
First of all, start the MYSQL and APACHE service by typing in the following commands on the terminal:
service apache2 startAfter running the service I will browse to the location where I have copied the DVWA folder. I have renamed it as ‘master’.
service mysql start
http://localhost/master
It will take you to the login page now log in with the default password that is ‘admin’ and ‘password’.
Now we will check the CSRF attack on the Low security of DVWA.
Now after clicking the CSRF on the left side, it will ask you to change the password. Now put anything and change the password. After changing the password right click and view the source code.
Now we will copy the following form code and change the form action to the following URL and save it in a text file.
http://localhost/master/vulnerabilities/csrf
Now I have renamed the file and saved it as csrf.html on the desktop.
Now open the file and enter the password you like and hit change.
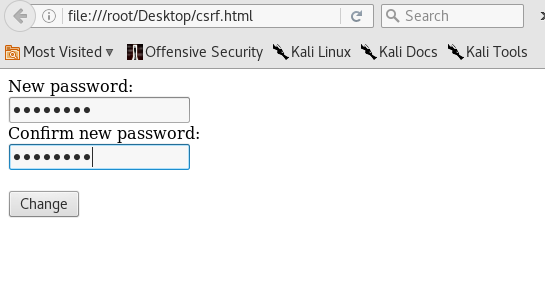
You will be redirected back to the original CSRF page and see that the password has been changed successfully.
Conclusion:
We saw that how a user can be tricked into performing unwanted actions that he does not want to do.A user could be tricked by social engineering attacks and could be compromised. Like you can send the malicious file to the user and if the user clicks the file you can compromise the security of the user.





