You can Download directory scanner from the following link:
WebSploit Directory Scanner
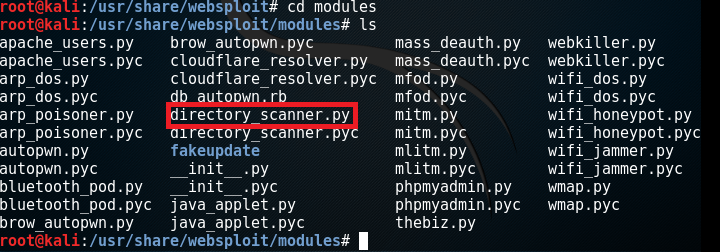
The above script is a modified script you need to replace previous one with this in the following directory:
/usr/share/websploit/modules/directory_scanner.py
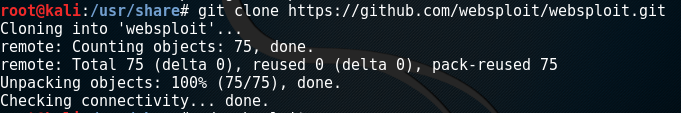
If you don’t have websploit installed use the following command to install it from Github
git clone https://github.com/websploit/websploit.git
Scanning Directories
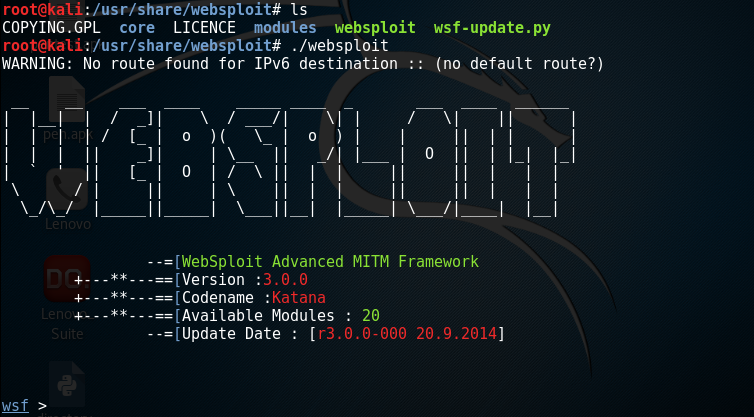
Now Run the websploit by typing in the following command:./websploit
You can see all the available modules using the following command:
Show modules
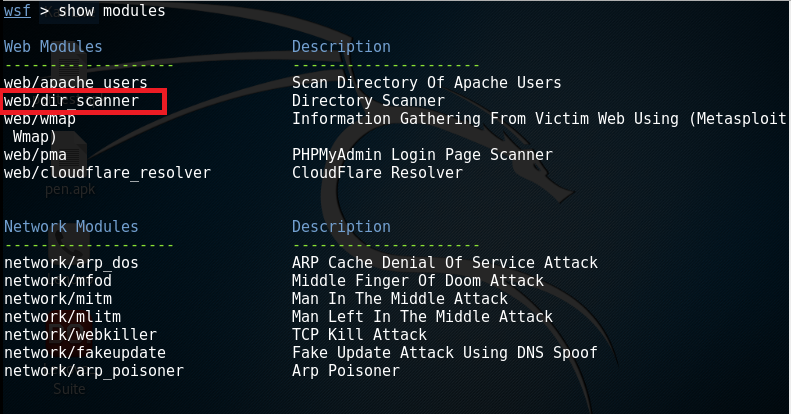
Here we will use web/dir_scanner module to scan for directories in a web server.
Type in the following command to use web/dir_scanner module:
Use web/dir_scanner
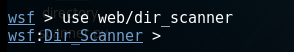
Now type in the following command to show all available options:
Show options
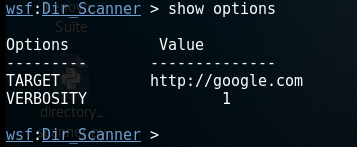
Here you can set the target and verbosity level for scanning. Google.com is set as the default target and verbosity level is set to 1.
Use the following command to set the target:
Set target [url]And set verbosity level by the following command:
Set verbosity 1If verbosity level is set to 0 it will show you directories with 302 and 200 code only, while verbosity 1 will show you all directories.
Now use the following command to run the scanner:
Run
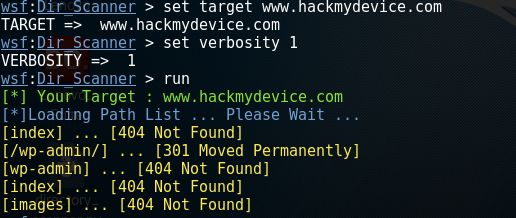
You can try it on your own site and scan for the directories. This scanner only scans for the following directories:
IndexIf you want to scan for custom directories you can edit the file in the following directory and place your own directories to scan for:
Wp-admin
Iimages
/usr/share/websploit/modules/directory_scanner.py
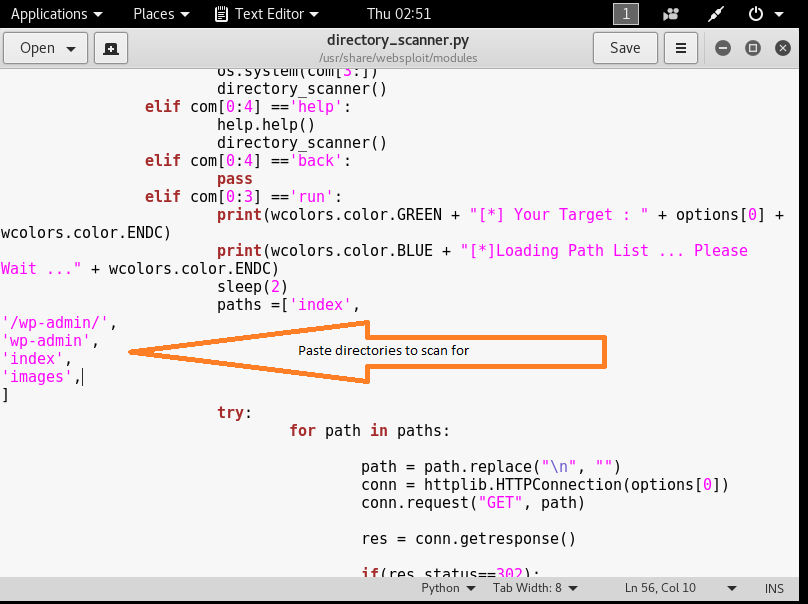
You can add directories there. Try to use the format /directoryname/ to prevent bad requests.

